----
iCloud Isn't Safe, Because Everyone's a Target and Apple Doesn't Care
// Gizmodo

Two years ago ago, tech writer Mat Honan wrote a blockbuster story for Wired, describing how a child got into his iCloud account and briefly ruined his life. You may have heard that the same thing recently happened to some very famous women, almost certainly using the same method. Apple is making it easy for you to be next.
In a bit of perfunctory apologia performed after the leak of dozens of naked private celebrity photos, Apple says it's not their fault:
We wanted to provide an update to our investigation into the theft of photos of certain celebrities. When we learned of the theft, we were outraged and immediately mobilized Apple's engineers to discover the source. Our customers' privacy and security are of utmost importance to us. After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple's systems including iCloud® or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.
To protect against this type of attack, we advise all users to always use a strong password and enable two-step verification. Both of these are addressed on our website at http://support.apple.com/kb/ht4232
This statement, which probably had several thousand pairs of lawyer eyeballs on it before it was sent to the press, is slippery. It hinges on very particular readings of words like "breach." Apple insists its iCloud service—which it touts as a seamless way of backing up your entire digital existence—was not "breached." This is maybe true in the sense that the celebrity nude traders didn't break or manipulate Apple code, but false and horribly misleading in the sense that they easily gamed Apple's system. And as Mat Honan will tell you, it's been that easy to get around for well over two years.
To fix this, Apple could have simply forced everyone to use two-factor verification for their accounts. It's easy, and would have probably prevented all of this. But Apple didn't do that (though you should still do it for yourself).
So, in the meantime, want to know how to get into someone's iCloud? It's this easy. Tell Apple you forgot that person's password, and then guess their security questions with readily available biographical information other Silicon Valley corporations have goaded us all into sharing.
But even as it acknowledges that its systems are easy prey for basic social engineering—a handful of Google or Facebook searches and a winning manner on the phone—Apple would like you to believe that you're not at risk. The celebrities whose private photos are now all over the internet, it declares, were victims of a "very targeted attack"—exposed only because they're public figures.
It's true that Kate Upton and Jennifer Lawrence were victims of a "very targeted attack." But the idea that only celebrities are being targeted is horseshit. There are people out there ripping the iCloud accounts of ordinary people, right now. iCloud will betray you whether you're McKayla Maroney or a kindergarten teacher.
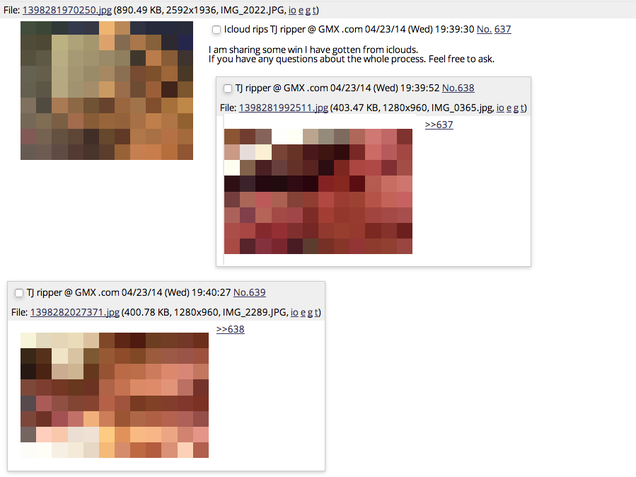
Over at AnonIB, a message board where the Jennifer Lawrence leak was possibly first floated, a band of "iCloud rippers" share the photos they've stolen from girls who are certainly not celebrities.
Friends, coworkers, classmates, and most of all, strangers: these rippers take requests from other AnonIB users (NSFW). In one AnonIB post, dated June 30th of this year, we see the following:
If there's any possible way, there's a very good chance of obtaining win from this girl I know. I have her password, and I've seen via icloud control panel that she has a 3.4gb incomplete backup. Hoping there's a way to rip whatever was backed up.
Another user asks for aid: "I downloaded it and tried to look up my ex's nudes, but it won't let me open the backup, any help?"
An AnonIB veteran is there to help:
To rip an Icloud you first need the email and password for the acct. How do you get the email/pass? well thats pretty easy actually.
You just need some very basic info that can usually be found on FB, Twitter, Instagram, Myspace, etc. and follow these 7 steps...
This guy has it down to a science:
Man I know the heart break lol All that hard work and nothing to show for it. But the best thing about Icloud is that they can always add a backup later. So just because you struck out today doesn't mean you shouldn't try again in a few months.
All the backups I got into personally I rip on a schedule.
January (Because girls get wild for christmas and new years)
April (Spring Break pics and tanning/work out pics cuz girls trying to get ready for summer)
August (End of summer and beginning of school yr)
November 1 (After Halloween)
The thread is full of looted photos of absolute nobodies, given away for free. To them, it's a sport or hobby. It's absolutely not a "targeted attack"—it's a casual free-for-all, taking advantage of Apple's pathetic security system. And this is just one website on a very big internet.
Apple won't acknowledge how vulnerable iCloud is, of course—not with new iPhones to unveil in exactly a week. And really, do you think the company that told us to hold our defective iPhones differently will admit your naked sexts are easy to steal? This is the house of arrogance that Steve Jobs built, and it's on the verge of releasing a new version of iOS that backs up not just your last 1,000 iPhone photos, but all of them, along with your digitized health data. This is the last company on Earth you should want feeling too proud to admit it fucked up.
Image by Jim Cooke
To contact the author of this post, write to biddle@gawker.com
----
Shared via my feedly reader
Dwight A. Hunt, Sr. A+, MCP
Facebook and Twitter: dahuntsr
Blogs:
Books, Podcasts, Old Time Radio & Movie instant stream reviews: http://audio-book-
Tech articles, firearms & all other posts: http://dahuntsr.
No comments:
Post a Comment